rsa timing based side chanel attack | cache side channel attack rsa timing based side chanel attack The execution time for the square-and-multiply algorithm used in modular exponentiation depends linearly on the number of '1' bits in the key. While the number of '1' bits alone is not nearly enough information to make finding the key easy, repeated . See more This is simply done by opening downloaded Go3 application on your LG, Samsung or Android TV. To add a device you can use two methods: Scanning QR code visible on a TV screen with your mobile phone. Adding the code you see on your TV screen to the following link https://go3.lv/subscriber/connect-tv.
0 · side channel blinding attack
1 · side channel attacks 2017
2 · side channel attack wikipedia
3 · side channel attack definition
4 · cpu side channel attack
5 · cache side channel attack
11 reviews. #42 of 93 Bakeries in Las Vegas Bakeries, Cafe. 6545 S Fort Apache Rd Suite 130, Las Vegas, NV 89148-6752. +1 702-246-2888 + Add website. Open now 6:00 AM - 3:00 PM. Improve this listing. See all (22) Ratings and reviews. 4.5. 11 reviews. #42. RATINGS. Food. Service. Value. Details. CUISINES. Cafe. View all details.
Timing attacks are difficult to prevent and can often be used to extend other attacks. For example, in 2018, an old attack on RSA was rediscovered in a timing side-channel variant, two decades after the original bug. See moreIn cryptography, a timing attack is a side-channel attack in which the attacker attempts to compromise a cryptosystem by analyzing the time taken to execute cryptographic algorithms. Every logical operation in a . See moreTiming attacks are easier to mount if the adversary knows the internals of the hardware implementation, and even more so, the cryptographic system in use. Since cryptographic security should never depend on the obscurity of either (see security through . See moreMany cryptographic algorithms can be implemented (or masked by a proxy) in a way that reduces or eliminates data-dependent timing . See more
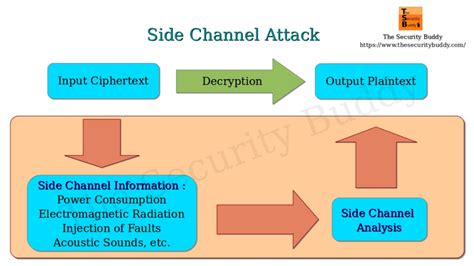
The execution time for the square-and-multiply algorithm used in modular exponentiation depends linearly on the number of '1' bits in the key. While the number of '1' bits alone is not nearly enough information to make finding the key easy, repeated . See more• Paul C. Kocher. Timing Attacks on Implementations of Diffie-Hellman, RSA, DSS, and Other Systems. CRYPTO 1996: 104–113 See moreIn computer security, a side-channel attack is any attack based on extra information that can be gathered because of the fundamental way a computer protocol or algorithm is implemented, rather than flaws in the design of the protocol or algorithm itself (e.g. flaws found in a cryptanalysis of a cryptographic algorithm) or minor, but potentially devastating, mistakes or oversights in the implementation One common side-channel timing attack is the Prime+Probe³ attack. In this attack, the adversary fills caches with his own data (Prime), then waits for the victim’s process to .
To understand the idea behind time-based side-channel attacks, recall that two famous public-key algorithms, RSA and Di e-Hellman key ex- change, require discrete exponentiation with large .These attacks aim at recovering a secret manipu-lated by cryptographic algorithms, by analyzing various sources of side-channel leakages (time, power consumption, electromagnetic (EM) .
side channel blinding attack
Based on our timing model, we launch successful timing attacks on RSA running on a GPU, extracting the private key of RSA. We also present an effective error detection and correction . Based on our timing model, we launch successful timing attacks on RSA running on a GPU, extracting the private key of RSA. We also present an effective error detection and .Timing attacks against RSA. Side-channel attacks exploit physical parameters such as execution time, supply current and electromagnetic emission to retrieve secrets from a system.In this work we present CacheBleed—the first side-channel attack to exploit cache-bank conflicts. In Section 3, we describe how CacheBleed creates contention on a cache bank and .
Timing attacks are difficult to prevent and can often be used to extend other attacks. For example, in 2018, an old attack on RSA was rediscovered in a timing side-channel variant, two decades after the original bug.Slowly becoming a bigger concern: new side-channels (VMs), better attacks. Side-channel attacks are more commonly used to attack trusted/embedded hw. E.g., chip running cryptographic operations on a smartcard. Often these have a small attack surface, not many other ways to .
Timing attack — attacks based on measuring how much time various computations (such as, say, comparing an attacker's given password with the victim's unknown one) take to perform. Power-monitoring attack — attacks that make use of varying power consumption by . One common side-channel timing attack is the Prime+Probe³ attack. In this attack, the adversary fills caches with his own data (Prime), then waits for the victim’s process to execute and .To understand the idea behind time-based side-channel attacks, recall that two famous public-key algorithms, RSA and Di e-Hellman key ex- change, require discrete exponentiation with large secret integer exponents.
These attacks aim at recovering a secret manipu-lated by cryptographic algorithms, by analyzing various sources of side-channel leakages (time, power consumption, electromagnetic (EM) radiations, etc) dur-ing their execution on a hardware device.Based on our timing model, we launch successful timing attacks on RSA running on a GPU, extracting the private key of RSA. We also present an effective error detection and correction mechanism. Our results demonstrate that GPU acceleration of RSA is . Based on our timing model, we launch successful timing attacks on RSA running on a GPU, extracting the private key of RSA. We also present an effective error detection and correction mechanism. Our results demonstrate that GPU acceleration of RSA is vulnerable to side-channel timing attacks.
Timing attacks against RSA. Side-channel attacks exploit physical parameters such as execution time, supply current and electromagnetic emission to retrieve secrets from a system.In this work we present CacheBleed—the first side-channel attack to exploit cache-bank conflicts. In Section 3, we describe how CacheBleed creates contention on a cache bank and measures the timing variations due to conflicts. We use CacheBleed to attack the scatter-gather implementation of RSA in the current version of OpenSSL (1.0.2f). After
side channel attacks 2017
Timing attacks are difficult to prevent and can often be used to extend other attacks. For example, in 2018, an old attack on RSA was rediscovered in a timing side-channel variant, two decades after the original bug.
Slowly becoming a bigger concern: new side-channels (VMs), better attacks. Side-channel attacks are more commonly used to attack trusted/embedded hw. E.g., chip running cryptographic operations on a smartcard. Often these have a small attack surface, not many other ways to .
Timing attack — attacks based on measuring how much time various computations (such as, say, comparing an attacker's given password with the victim's unknown one) take to perform. Power-monitoring attack — attacks that make use of varying power consumption by . One common side-channel timing attack is the Prime+Probe³ attack. In this attack, the adversary fills caches with his own data (Prime), then waits for the victim’s process to execute and .To understand the idea behind time-based side-channel attacks, recall that two famous public-key algorithms, RSA and Di e-Hellman key ex- change, require discrete exponentiation with large secret integer exponents.These attacks aim at recovering a secret manipu-lated by cryptographic algorithms, by analyzing various sources of side-channel leakages (time, power consumption, electromagnetic (EM) radiations, etc) dur-ing their execution on a hardware device.
Based on our timing model, we launch successful timing attacks on RSA running on a GPU, extracting the private key of RSA. We also present an effective error detection and correction mechanism. Our results demonstrate that GPU acceleration of RSA is .
Based on our timing model, we launch successful timing attacks on RSA running on a GPU, extracting the private key of RSA. We also present an effective error detection and correction mechanism. Our results demonstrate that GPU acceleration of RSA is vulnerable to side-channel timing attacks.Timing attacks against RSA. Side-channel attacks exploit physical parameters such as execution time, supply current and electromagnetic emission to retrieve secrets from a system.

side channel attack wikipedia
side channel attack definition
Located just minutes from the Las Vegas Strip, Gold Coast Hotel & Casino offers true locals hospitality, a place where locals and visitors alike can feel at home.
rsa timing based side chanel attack|cache side channel attack